About me
Aspiring Cybersecurity Analyst | Cloud Computing Enthusiast
Portfolio: https://nasirsyed-portfolio.com/
🎓 Graduated with a B.S. in Computer Science, concentration in Cybersecurity, from UNC Charlotte (May 2025). Experienced in network security, cloud computing, and operating systems administration.
🔒 Network Security & Compliance:
• Certified in Computer Networks, Security, and Cybersecurity Compliance (NIST, ISO). Experienced in
firewall
configuration, access control, and vulnerability management.
☁️ Cloud Computing:
• Experience with AWS, Azure, Google Cloud, Vultr, and EdgeUno. Proficient in deploying and managing virtual
machines,
cloud security, and resource allocation.
💻 Programming:
• Proficient in Python, C, C++, Java, JavaScript, TypeScript, Express.js, Node.js, HTML, CSS, Flask,
Bootstrap, and Bash.
🖥️ Operating Systems:
• Strong expertise in administering and securing both Windows and Linux environments, including user
management, scripting
for automation, and system monitoring.
🛠️ Tools & Databases:
• Skilled in Wireshark for traffic analysis, GitHub for version control, MySQL and MongoDB for database
management, and
VSCode/Apache NetBeans for development.
I'm passionate about leveraging cloud technology to build secure, scalable systems and protect the digital world. Let’s connect if you share an interest in cybersecurity!
What I'm doing
-
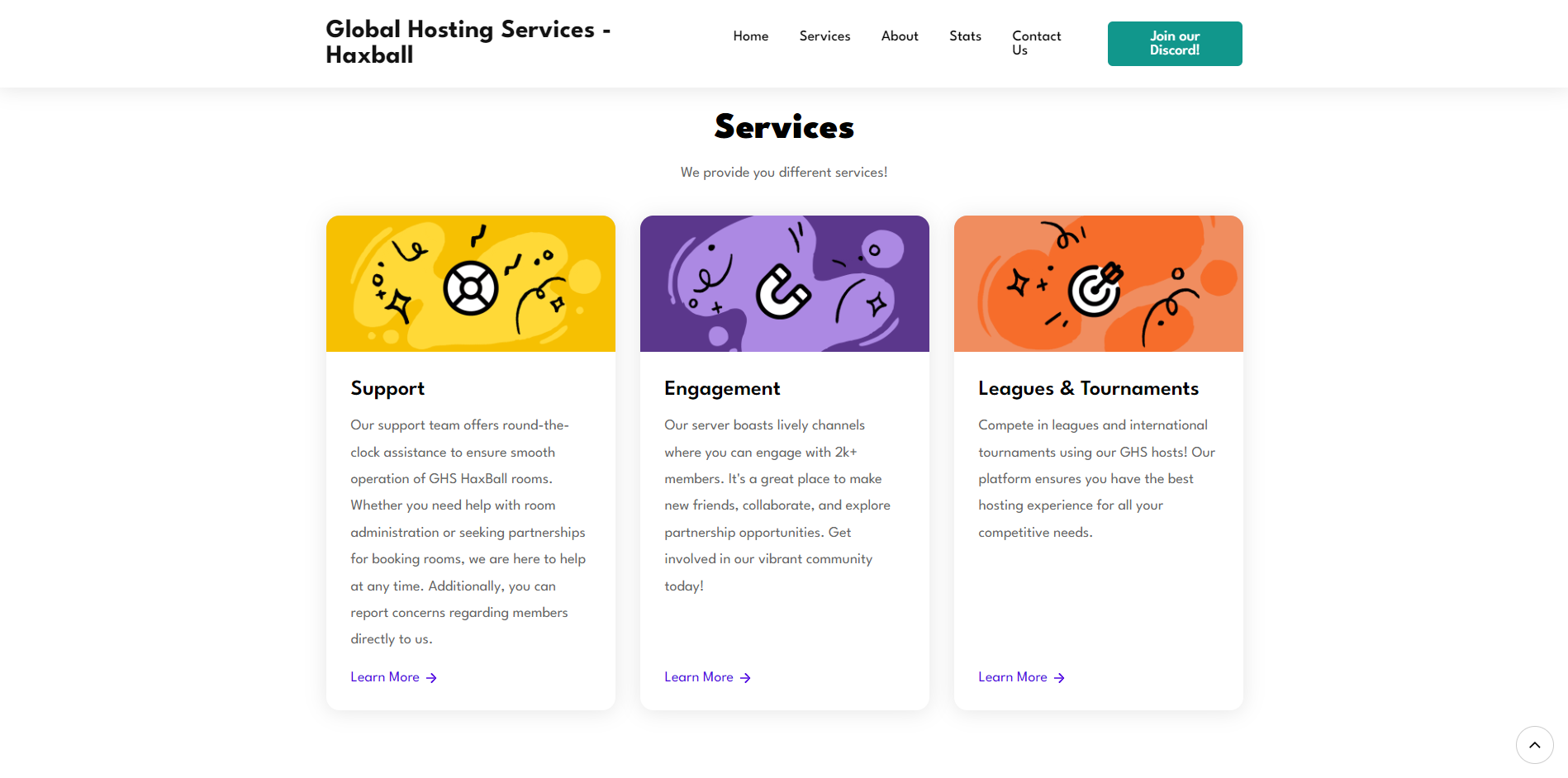
Full-Stack Web Development
Developing web applications using modern frameworks like Express.js and Flask, integrating MongoDB for database management, and implementing user authentication, session management, and data authorization features.
-
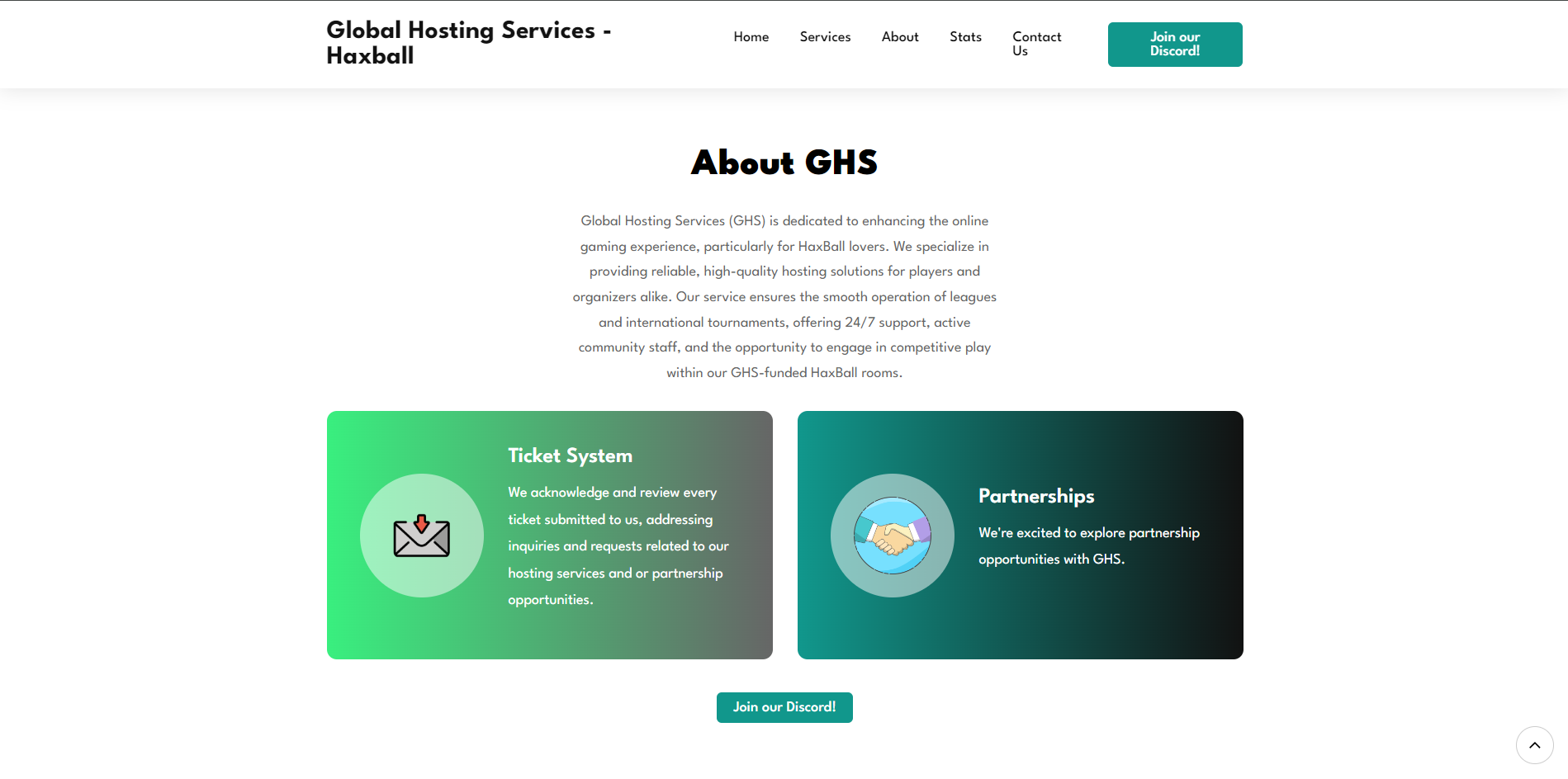
Cloud Infrastructure and Automation
Managing and optimizing cloud infrastructure using platforms like AWS, Google Cloud, and Azure. Additionally, using tools like Ansible and Bash scripting for automation and maintaining private network environments, including deploying LXC containers.
-
Cybersecurity and Vulnerability Exploitation
Working on identifying and exploiting vulnerabilities like CSRF, XSS, broken access control, and SQL injection, as well as performing network security tasks such as traffic analysis, DNS configuration, and secure network design.